
ISMS-Kit (Information Security Management System)
You are the IT expert – we offer you a complete systematic guide to setting up an ISMS with all the necessary documentation templates.
- For small and medium-sized enterprises
- In accordance with ISO 27001 or VDA-ISA (TISAX)
- Practical and user-friendly
- Quick success in implementation and execution
What is an ISMS (information security management system)?
An information security management system (ISMS) serves to ensure the information security objectives of confidentiality, integrity, and availability of information. It identifies and addresses risks, continuously improves security measures, and creates security awareness within the organization.
In addition to guidelines and specifications, effective processes and procedures, suitable organizational structures, and technical and organizational protection functions in software and hardware are necessary for an ISMS to be effective.
ISMS Kit
The ideal toolkit for IT experts
- ISMS manual: Structured according to the ISO high-level structure.
- Individual application: Can be used for certification according to ISO 27001 and VDA-ISA/TISAX or to comply with the NIS2 directive to be introduced by national law.
- Documentation templates: Tested templates and checklists.
- Assignment of rights: Department-based access.
- Central document storage: Structured and clear management.
- Versioned archiving: Secure archiving in accordance with ISO standards.
- Employee training: eLearning modules on information security and data protection available.
- Optional: Web-based training for ISMS officers: Further information is available here. here.
When does a company need an ISMS?
- Clear guidelines for the IT department for creating a comprehensive manual for protecting sensitive information and minimizing risks and dangers from hacking, data encryption, and other security incidents.
- Compliance with legal requirements such as the NIS2 Directive (KRITIS, etc.), which is to be implemented nationally.
- As part of ISO 27001 or VDA-ISA/TISAX certification.
- Compliance with industry standards.
An ISMS offers companies a structured approach to information security, improves resilience to cyberattacks, and increases competitiveness.
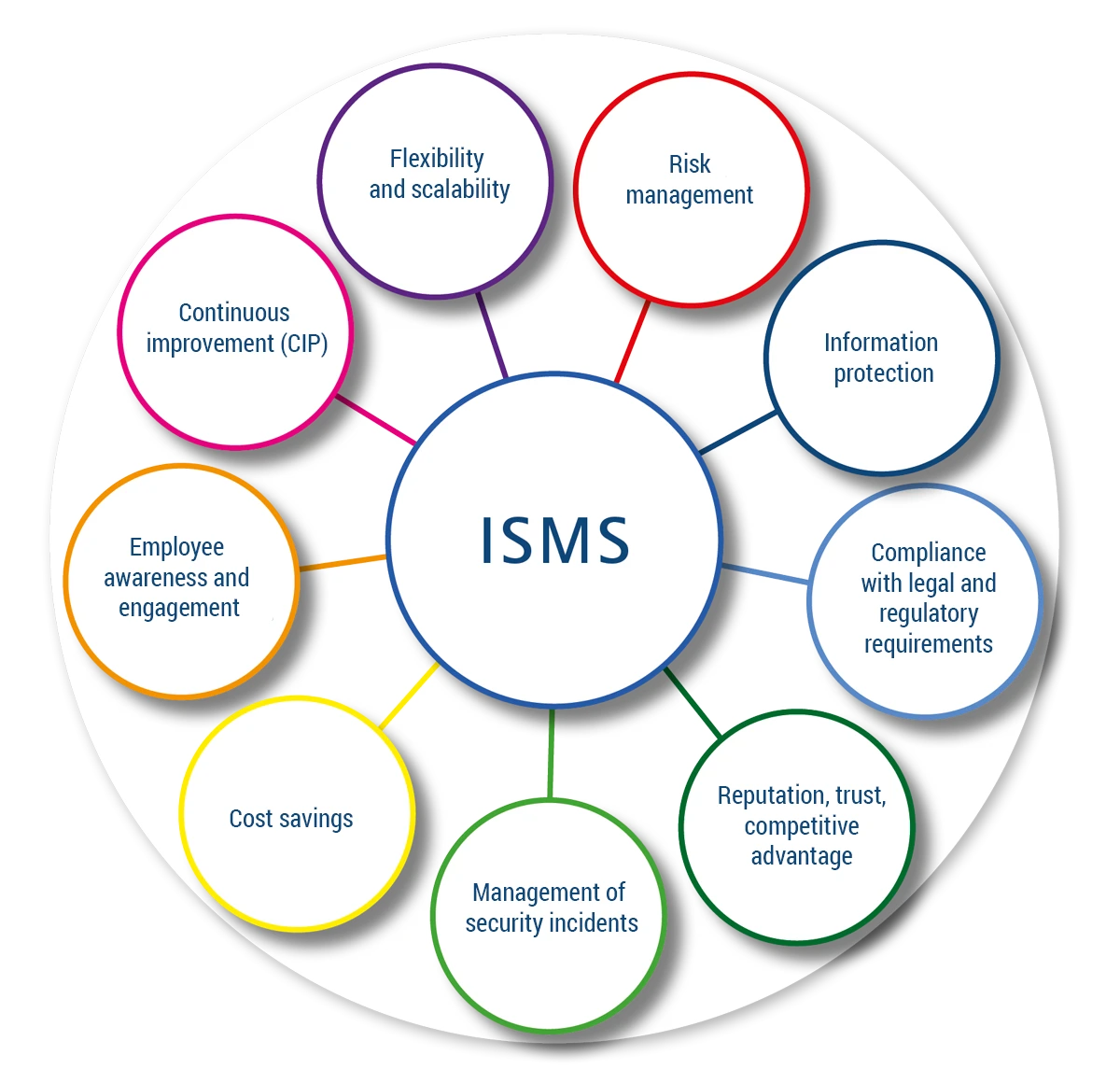
9 advantages of an ISMS
according to ISO 27001 or VDA-ISA/TISAX
- Identification, assessment, and handling of information security risks
- Protection of confidential information and prevention of loss or theft
- Compliance with all relevant data protection and information security laws, regulations, and standards
- Confidence-building measures toward customers, partners, and stakeholders, and competitive advantage due to demonstrable commitment to information protection
- Appropriate response to a security incident through policies and processes
- Prevention of financial losses and costly disputes by avoiding security incidents and information loss
- Promotion of security awareness among employees and active participation in the protection of company information
- Continuous monitoring and improvement of information security (CIP)
- Rapid adaptation to changing conditions and risks
How do you go about introducing an ISMS in your company?
- Strategic planning: Strategic planning is the responsibility of senior management. It sets guidelines and goals and provides resources.
- Operational implementation: Operational implementation is carried out by project teams or information security staff.
- Practical support: The ISMS Kit provides resources, training, and guidance for implementation.
- Understanding of roles: Every employee contributes to information security. Therefore, all employees must be involved in achieving information security goals.
- eLearning: Employee training is an important factor in the effective and sustainable implementation of the ISMS. It aims to create an understanding of information security policies, promote risk awareness, and teach security practices.
Holistic approach: A holistic approach is crucial for an ISMS. It must therefore be understood as a continuous process that is integrated into the corporate culture.
Web-based training for ISMS officers

Support your employees with web-based training to become ISMS officers. The seminar is aimed at individuals who are responsible for setting up and managing an ISMS in their company. In 10 clearly structured modules, participants learn the basics they need to set up and manage an ISMS in their company. The training can be activated in the ISMS Kit.
Café Datenschutz provides information about the ISMS Kit
Introduction to ISMS (german)

Presentation of ISMS Kit (german)

Do you require further information?
Our YouTube channel, Café Datenschutz, offers you an extensive playlist on the topic of “information security management” and explains in several videos how and when the ISMK Kit can be important for you.
An ISMS can offer a wide range of functions aimed at ensuring the security and integrity of information within a company. These include risk assessment, security policies, access control, monitoring, incident response, and compliance management. In addition, it often includes functions such as training and awareness measures for employees, regular security audits and reviews, and continuous improvement processes to keep pace with constantly changing threats and requirements.
Yes, most ISMSs are scalable and can be expanded as needed to address growing security requirements. They can be adapted to the specific requirements and size of a company, whether it is a small start-up or a large multinational corporation. The scalability of the ISMS allows for flexible adaptation to changes in the company structure, the scope of data to be protected, and evolving threat landscapes.
An ISMS can store sensitive and confidential data such as customer information, intellectual property, financial data, and compliance documentation to ensure that it is adequately protected and managed.
Security functions of an ISMS can include access control, encryption, intrusion detection, incident response, and regular security reviews. In addition, functions such as security awareness training for employees, security policies and procedures, backup and recovery mechanisms, and security audits can also be part of a comprehensive ISMS.
Yes, an ISMS can be integrated with other systems such as IT management tools, compliance systems, and network security solutions to enable seamless collaboration and a holistic approach to securing information and systems. Integrations allow data to be exchanged between different systems and automated processes to be implemented, improving the efficiency of security measures and reducing response times to security incidents.

